Most IT leaders think partners, customers make their business a ransomware target - Help Net Security
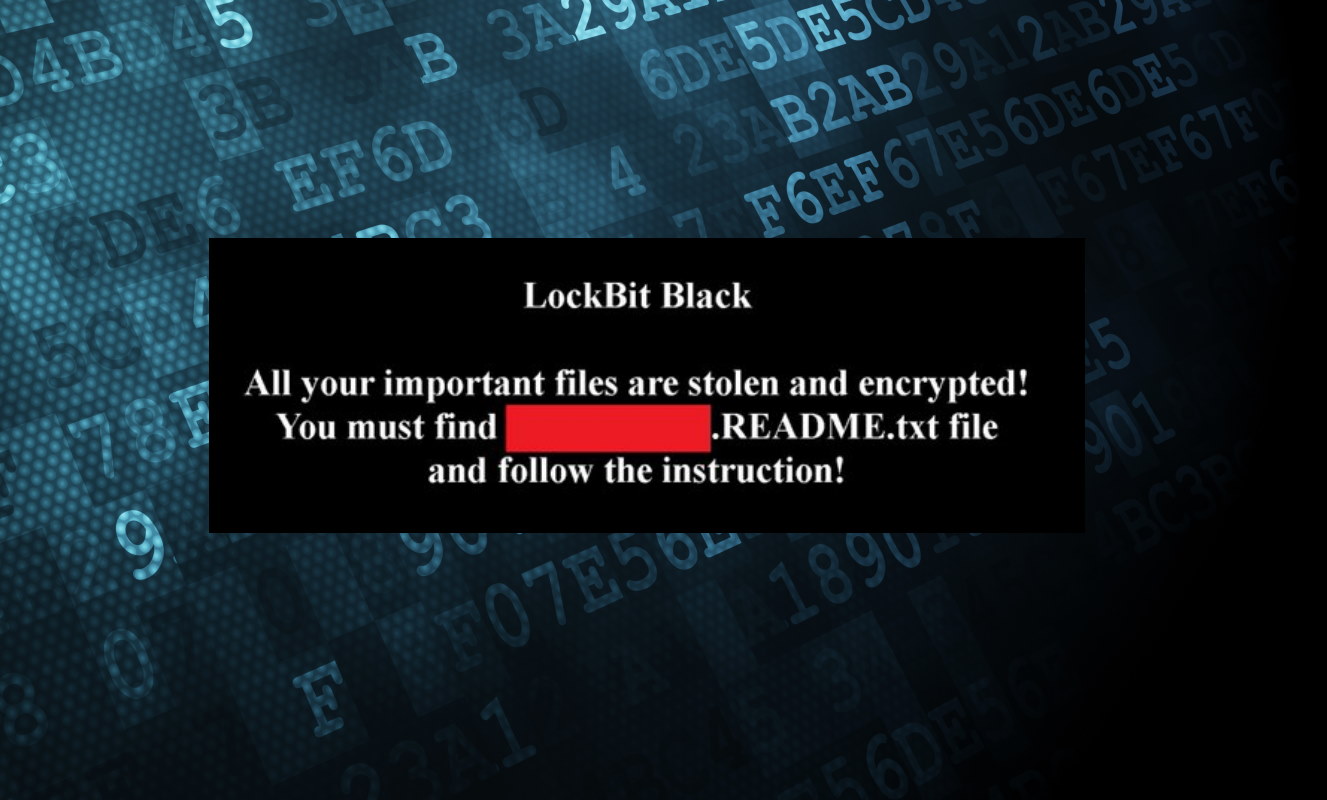
Trend Micro details LockBit 3.0 ransomware that imitates BlackMatter capabilities - Industrial Cyber
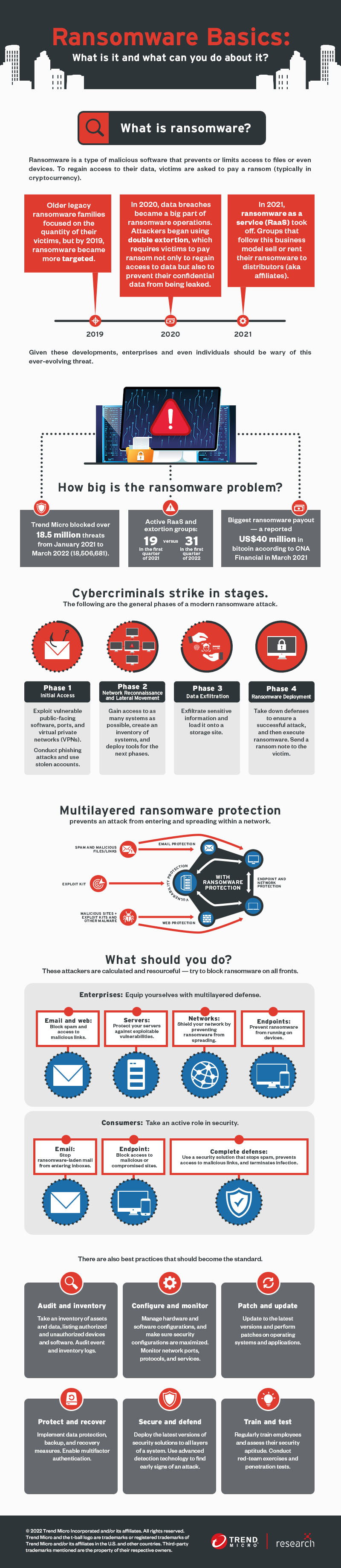
![The Cyber Security Hub.com - Ransomware Rescue Plan [via Trend Micro] #computerscience #computerengineering #cybersecurity #infosec #riskmanagement #encryption #IoT #AI #dataprotection #privacy #hacking #hacker #pentest #tech #datascience #code #coding ... The Cyber Security Hub.com - Ransomware Rescue Plan [via Trend Micro] #computerscience #computerengineering #cybersecurity #infosec #riskmanagement #encryption #IoT #AI #dataprotection #privacy #hacking #hacker #pentest #tech #datascience #code #coding ...](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=1196623230689007)
The Cyber Security Hub.com - Ransomware Rescue Plan [via Trend Micro] #computerscience #computerengineering #cybersecurity #infosec #riskmanagement #encryption #IoT #AI #dataprotection #privacy #hacking #hacker #pentest #tech #datascience #code #coding ...

Trend Micro: Hackers target hospitals during COVID-19 pandemic, many are still vulnerable - SoyaCincau

Trend Micro Maximum Security Review | Trend Micro vs Ransomware | Ransomware Protection Test | 2021 - YouTube

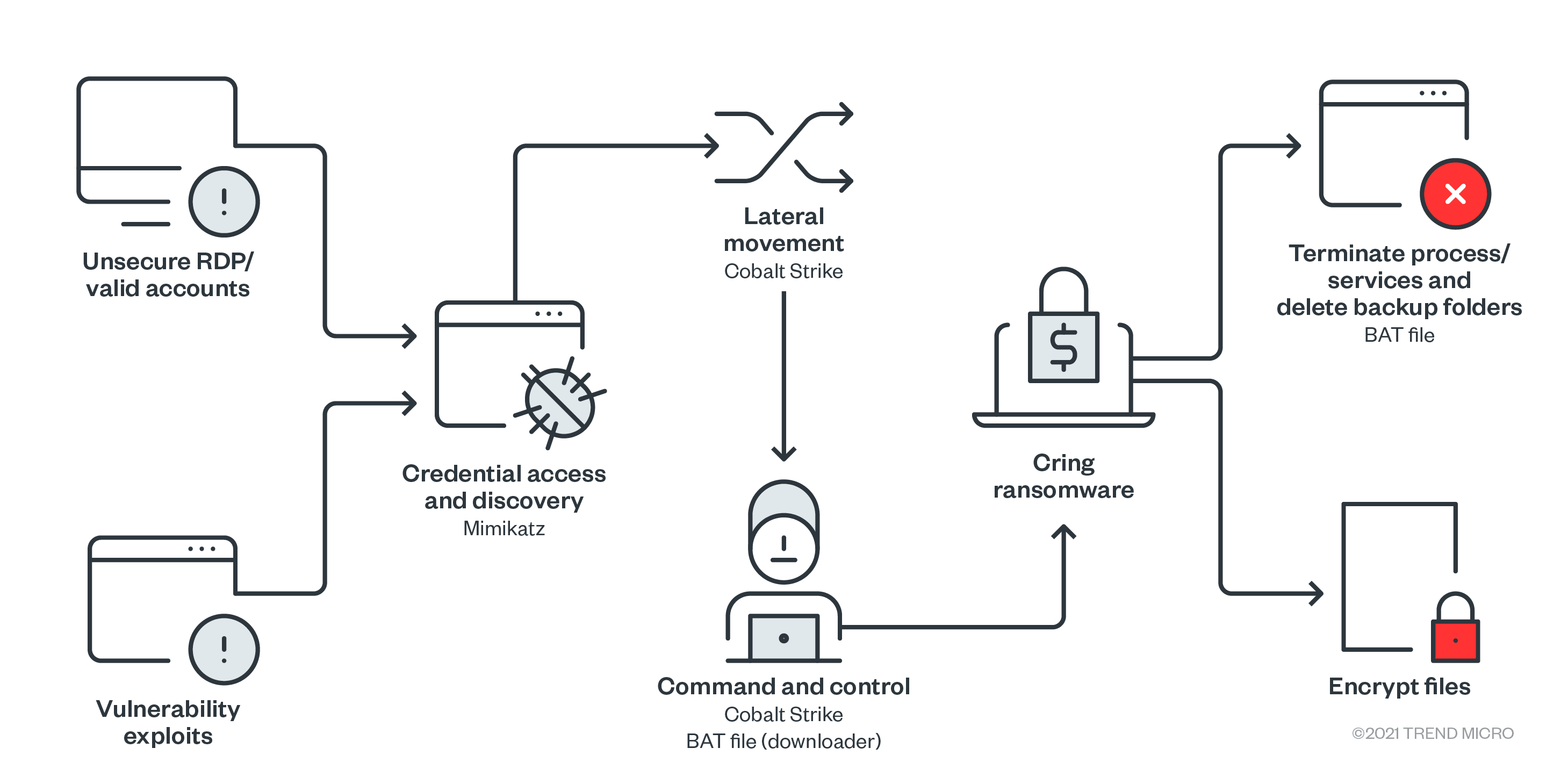
Trend Micro - Hive operates as a ransomware as a service (RaaS) network. The group constantly refines its malware tools and tactics to stay ahead of competition. Read more to learn about

Hackers: Trend Micro creates 'honeypot' to analyse security threats, gets subjected to ransomware & cryptocurrency mining - The Economic Times

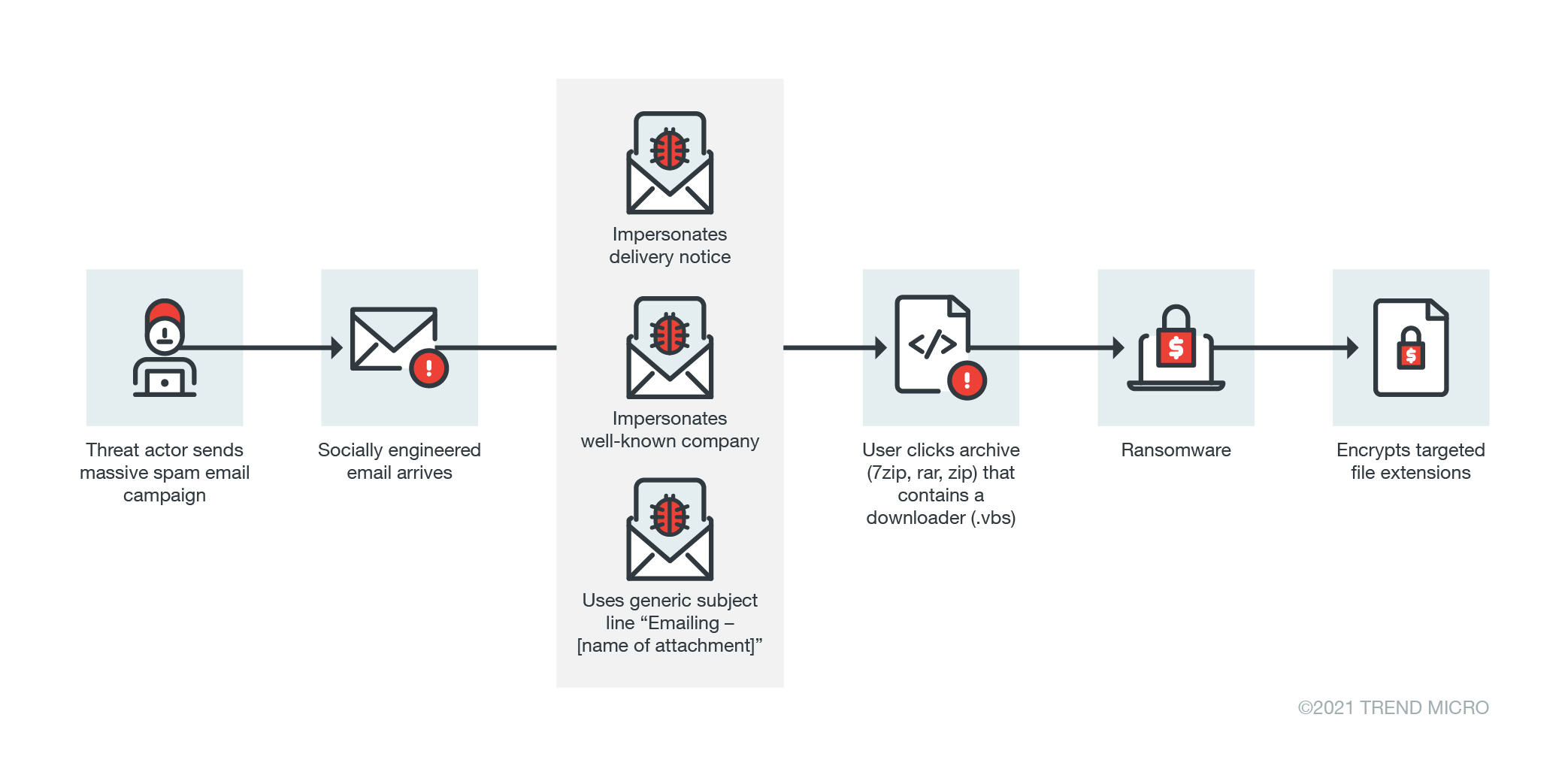
Virus Bulletin on Twitter: "Trend Micro researchers look into AvosLocker ransomware samples that make use of a legitimate driver file to disable anti-virus solutions. The ransomware is also capable of scanning multiple

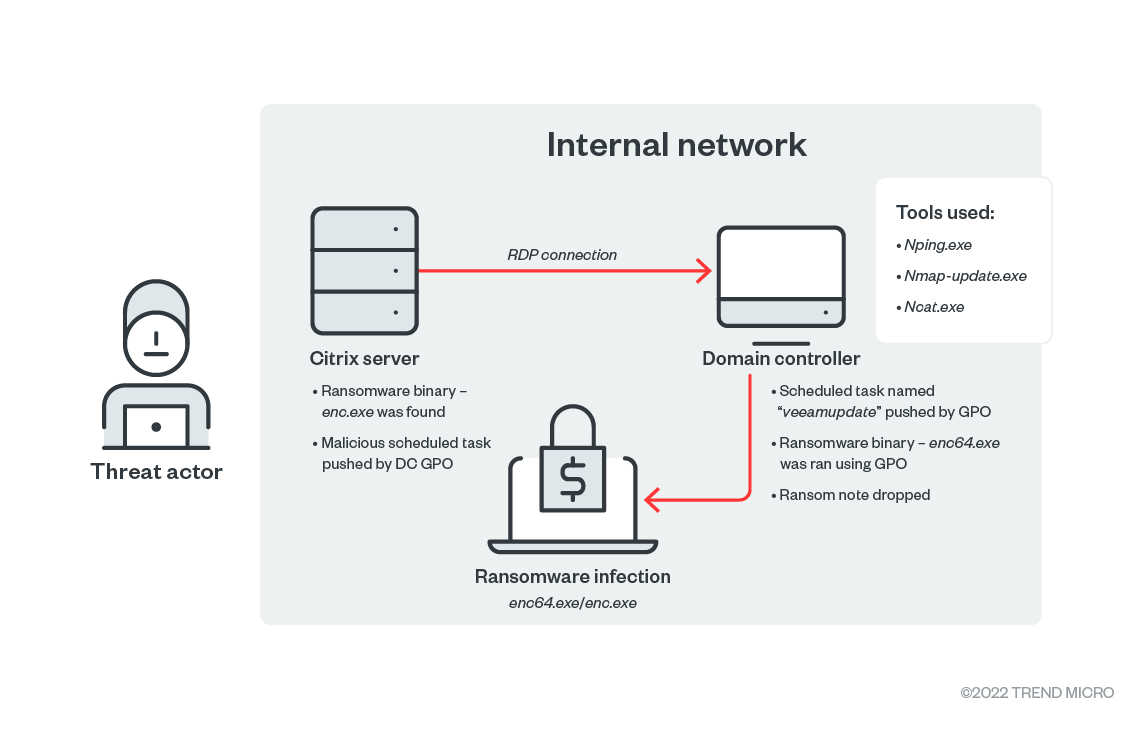
![Trend Micro Ultimate Security (10-Device) (1-Year Subscription) [Digital] TRE021800G701 - Best Buy Trend Micro Ultimate Security (10-Device) (1-Year Subscription) [Digital] TRE021800G701 - Best Buy](https://pisces.bbystatic.com/image2/BestBuy_US/images/products/6453/6453108_sd.jpg;maxHeight=640;maxWidth=550)